
Similar Posts

Engage employees, improve productivity, and build team cohesion
After so much turmoil and change, employees all want different things. Companies need to support a successful back-to-hybrid-office life—a situation that is here to stay. The capabilities for positive hybrid meetings is possible with modern Microsoft tooling like Teams, Endpoint Manager, and devices like Surface Hub. Immersive and custom engagements that highlight leading guidance and…

New Zealand moves to a cloud-based identity solution for its 4.9 million residents
The New Zealand Department of Internal Affairs partnered with UNIFY Solutions to migrate the country’s RealMe identity service—more than 6 million sign-ins and authentications spanning 163 government services and 56 agencies—to Microsoft Azure Active Directory B2C, part of Microsoft Entra.


Customer Lifetime Value and the Subscription Economy
In our digital world, subscription services are more complicated. Specifically, a business’s costs, benefits and value of subscriptions are more complex. It’s no longer as simple as multiplying the cost of the subscription by the number of months and subtracting the costs associated with acquiring the customer and publishing and delivering the magazine. Think about…
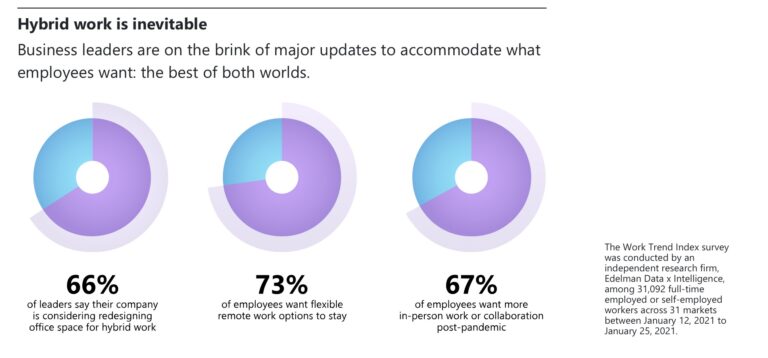
Hybrid Work is Inevitable
67% of business leaders struggle with collaboration in remote settings. How about your company? Read the infographic and reach out to a @Microsoft expert from One Php Technology, Inc. to optimize your #hybridwork environment.

