
Similar Posts

Microsoft Edge as default browser for access to legacy web apps and better security
Today’s users are looking for more ways to remain productive while working on any device. Businesses have security top of mind, and so with those two goals, Global healthcare company GlaxoSmithKline chose Microsoft Edge as its single web browser. The IT team responsible for the Microsoft Edge deployment of over 130,000 employees enrolled every Windows…
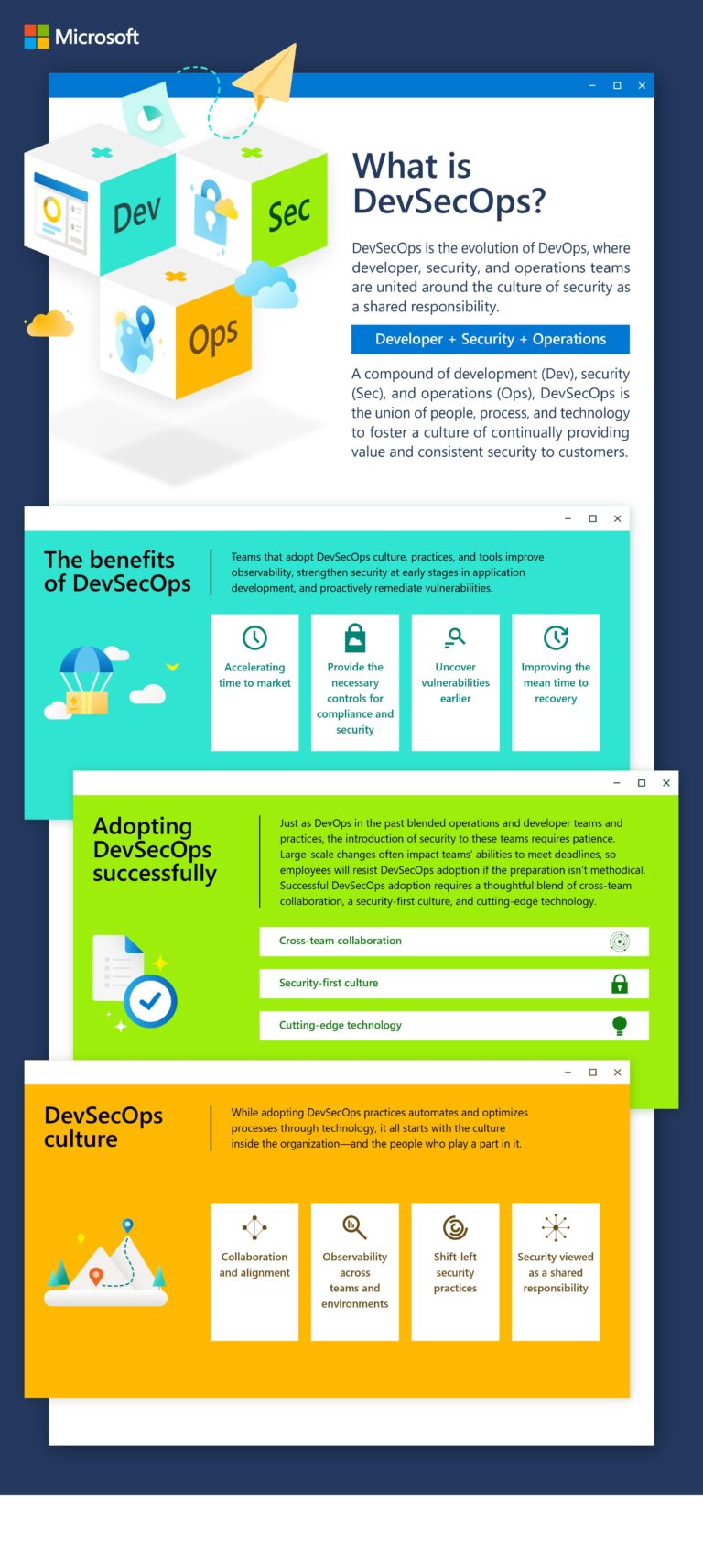
What is DevSecOps?
DevSecOps is the evolution of DevOps, where developer, security, and operations teams are united around the culture of security as a shared responsibility. Sign up to stay connected. We’ll help you navigate the world of DevSecOps and understand how to successfully adopt it.

Introducing Password Removal for Microsoft Accounts
Common attacks such as phishing, password spray, and credential stuffing rely on one unchanging truth: when it comes to passwords, human behavior is predictable. Armed with this predictability, bad actors still succeed most of time when attempting these types of attacks, even though the tools they’re using are 30 years old. Starting today, we’re excited…

Get the most out of Microsoft Azure with Visual Studio
If you have a Microsoft Visual Studio subscription, make sure you explore the benefits that come with it—or you may be leaving value on the table. Use your monthly Microsoft Azure credits and Azure training, DevTest pricing, Azure DevOps, support, and more. Get an overview of all your benefits and even project ideas for how…
Big Red Cloud: Targeting pain points
Chief Executive Marc O’Dwyer shares that he started Big Red Cloud, an online cloud accounting software company, because as a business owner of a different company, he experienced problems with his own accounting systems and believed there had to be a better way. Because of these prior pains, he focuses on supporting customers and claims…
