
Similar Posts

Unify management and security with Microsoft cloud, apps, and endpoints
Today’s workers require adaptability since they often use various devices to accomplish tasks. Microsoft cloud, apps, and endpoints combine services you may already be using, such as Microsoft Intune, which are part of the Microsoft 365 stack designed to help secure access, protect data, and respond and manage risk. Use Endpoint Manager to deploy and…
What is DevOps?
DevOps as an ideal is revolutionizing the way organizations communicate and how they handle their daily work. Learn how this process brings together development and operations teams—who have traditionally been pitted against each other—and allows them to align on value and work toward a common goal.

Empower employees for secure remote work with Windows Virtual Desktop
Virtual desktops can provide great security to organizations and allow remote employees to access safely confidential organizational data. Learn how Windows Virtual Desktop makes your workflow secure in addition to optimizing services.
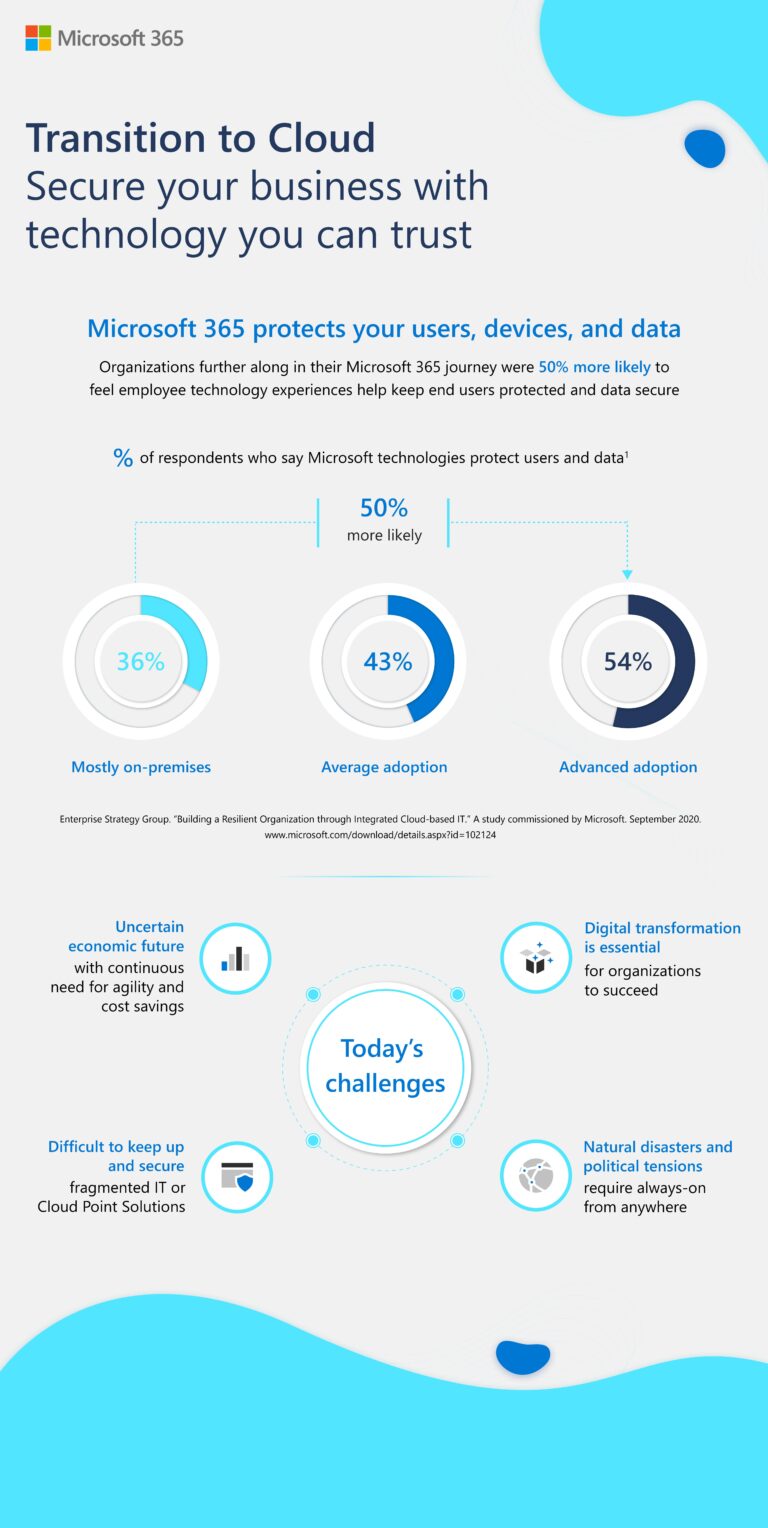
Transition to Cloud: Secure your business with technology you can trust
Today’s complicated virtual business reality makes it difficult to secure fragmented IT or cloud point solutions. As we’ve seen, natural disasters and political tensions require always-on from anywhere tech solutions. We know that Microsoft 365 helps businesses stay agile in these uncertain economic times with cost savings and cloud advances. Need proof? This infographic illustrates…

Get started with GitHub and Azure DevOps
Adopting the tools and mindset of DevOps in the right manner can facilitate development efficiency, boost productivity, and increase the rate at which products can be brought to market. Sign up to stay connected. We’ll help you navigate the world of GitHub and Azure DevOps and share helpful tips to get started.

