
Similar Posts
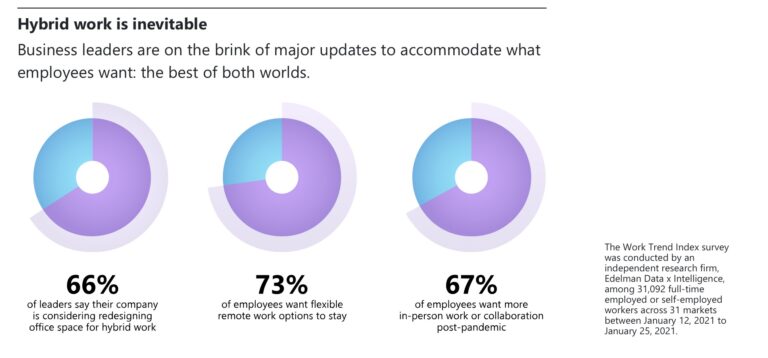
Hybrid Work is Inevitable
67% of business leaders struggle with collaboration in remote settings. How about your company? Read the infographic and reach out to a @Microsoft expert from One Php Technology, Inc. to optimize your #hybridwork environment.

5 Questions on the Minds of Hybrid Managers
Is it okay to exercise during meetings? When can I ask people to come into the office? Experts on the Future of Work share insights on creating happy hybrid teams Three years ago, Microsoft launched a new manager expectations framework designed to help deliver success through empowerment and accountability. The framework, called “Model, Coach, Care,”…

The Future of Hybrid Work: 5 Key Questions Answered with Data
The past year of COVID-19 variants has thrown a wrench in the return-to-office plan for many organizations. What was expected to be a mass migration back to the office in September of 2021 quickly halted as employers extended their work-from-home policies indefinitely into another miserable pandemic winter. As spring approaches, employees and employers once again…
The AI-enabled future
This article from Forbes explores Cognilytica’s four-part AI enabled vision of the future. In that vision, there are four main areas in which AI will impact our future lives: the way we work, the way we live, the way we experience the world and our interactions with each other, and the relationship we have with data.

Protect your endpoints with top EDR software
Companies must now consider endpoint detection and response software (EDR) with AI and machine learning capabilities, as well as threat intelligence databases, to function in a safer, evolving digital environment. However, most of the features users expect from popular EDR tools, such as device control, advanced threat targeting, and rollback, are either unavailable or require…

The Passwordless Future is Here for Your Microsoft Account
Nobody likes passwords. They’re inconvenient. They’re a prime target for attacks. Yet for years they’ve been the most important layer of security for everything in our digital lives—from email to bank accounts, shopping carts to video games. We are expected to create complex and unique passwords, remember them, and change them frequently, but nobody likes…
